
Safer with Google
Every Google product is designed for safety. It’s our responsibility to keep your personal information private, safe, and secure.
Jump to Content
We’re dedicated to keeping everyone’s data safe with the most advanced technology, operated by skilled, trusted professionals.



Every Google product is designed for safety. It’s our responsibility to keep your personal information private, safe, and secure.
With robust business continuity and disaster recovery measures in place, our data centers will shift access automatically to another data center in the event of a disruption. And our emergency backup generators continue to work even during power failures.

To ensure our data centers run reliably 24/7, our employees at our data center control stations (as shown in our Mayes County, Oklahoma, data center above) monitor the building and its power structure with the ability to take calls from the field, validate repair tickets, and authorize repairs.
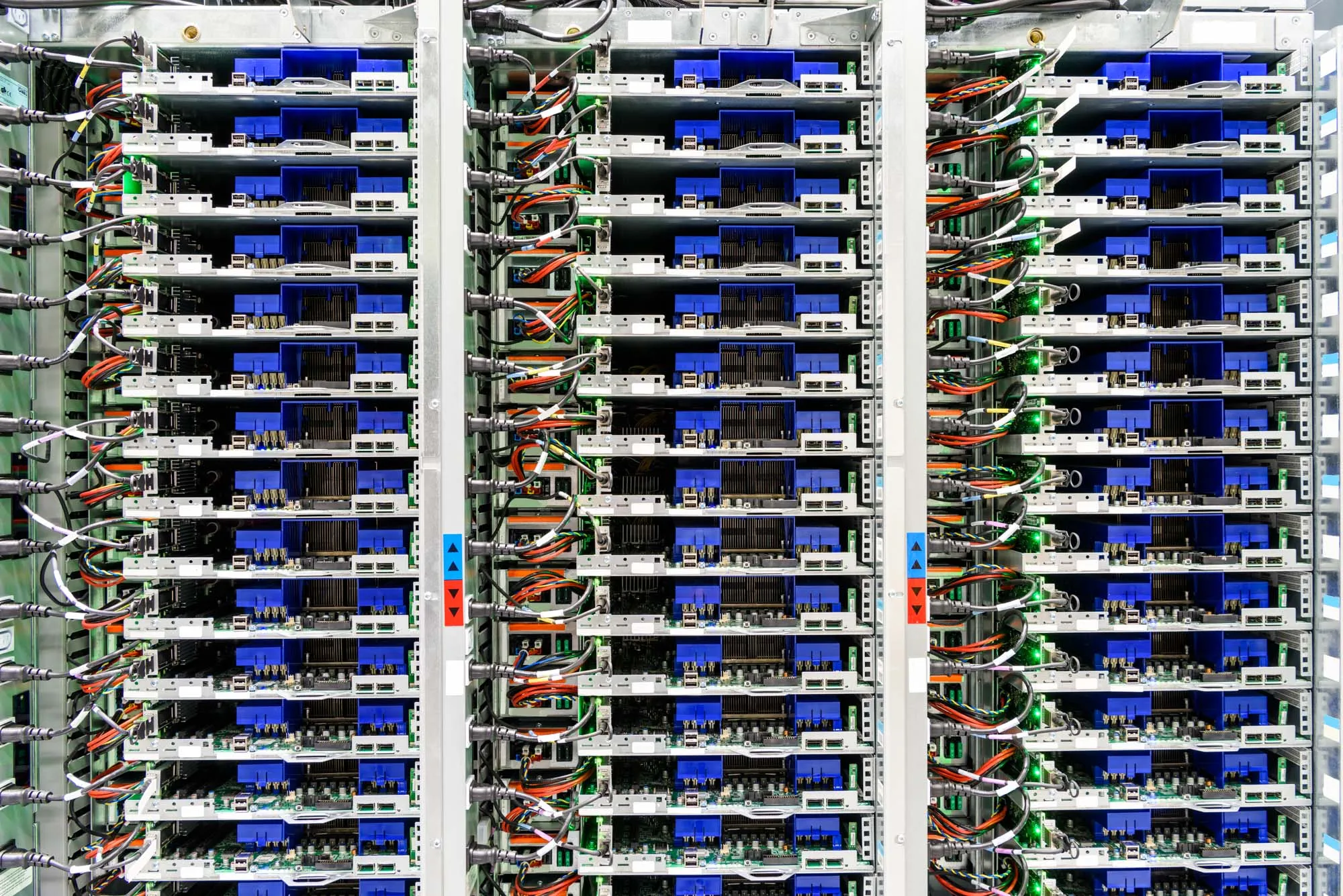
Google secures data through distributed, replicated servers.
We distribute all data across many computers in different locations, chunking and replicating it over multiple systems to avoid a single point of failure. We name these data chunks randomly to make them unreadable to the human eye.
See how our data centers are designed and operated with security in mind.
Layer One
Property boundaries
Signage and fencing surrounds the facility.
Layer Two
Secure perimeter
An anti-climb fence, vehicle crash barrier, overlapping thermal cameras, and 24/7 guard patrols protect the exterior.
Layer Three
Building access
Authorized access is required of everyone who enters the building, including multiple security checkpoints, ID badges, and iris scans to validate identity.
Tarik Billingsley
Google Data Centers Area Security Manager
Layer Four
Security operations center
This is the hive of the data center, where security teams monitor the facility 24 hours a day, 365 days a year.
Layer Five
Data center floor
Access to the actual server floor is highly restricted and involves multiple authentication factors.
Layer Six
Crusher room
This is where data storage devices are physically destroyed to prevent data recovery. Only authorized personnel have access to enter this secure storage unit.

Google Cloud’s multifaceted protection is built upon six progressive layers to deliver defense-in-depth. From the hardware that is Google-built and hardened to our custom-made infrastructure, any application within our system deploys securely, using multiple mechanisms to establish and maintain trust. We encrypt everything from communications over the internet to every piece of data at rest within our network, enabling distribution for availability and reliability.
Operational and device security
We do not assume any trust between services, and use multiple mechanisms to establish and maintain trust — we designed our infrastructure to be multi-tenant from the start.
Internet communication
We encrypt communications over the internet to our cloud services.
Identity
We strongly authenticate all identities, users, and services.
Storage services
Data stored on our infrastructure is automatically encrypted at rest and distributed for availability and reliability.
Service deployment
This service ensures that only the individual or service with the right identity, accessing the right machine, authorized by the right code is accessing the right data, at the right time and context.
Hardware infrastructure
By designing the components ourselves, we ensure they’re intentionally constructed to not include unnecessary components that could introduce vulnerabilities. Our custom built chip, Titan, establishes a hardware root of trust into our servers, reducing the risk of access gained through phished credentials.


To ensure continuous operations and services at our data centers, we have robust, ISO 22301:2019 certified business continuity and disaster recovery measures in place.